Information Technology Reference
In-Depth Information
Figure3 depicts the protection principle of
p
-cycle for link protection. The
p
-cycle in
Figure3(a) is pre-configured as a closed connection on the cycle A-G-F-E-D-C-B-A. On-
cycle links are shown in Figure3(b). Upon failure of the on-cycle link A-F, the
p
-cycle offers
protection by the route on the remainder of the cycle (G- F-E-D-C-B-A). Figure3 (c) shows
the protection of such a link (F-A) on straddling links. Two protection routes can be provided
for straddling links, i.e., the routes A-B-C-D-E-F and A-G-F in the example [16]. In practice,
one can protect two working capacity units of straddling links.
2.1.5. Segment Protection
In this scheme, working path is divided into multiple active segments and each working
path is protected with a backup segment (instead of protecting the whole working path in the
path protection scheme). This scheme is failure-dependent path protection, but the rerouted
traffic only needs to be from the node of the backup segment that protects the failed link [17].
To achieve bandwidth efficiency in links under path or segment protection schemes, backup
bandwidth allocated to different backup segments or backup paths can be shared. A tradeoff
between time and network utilization (or blocking execution) may be obtained using this
scheme [18].
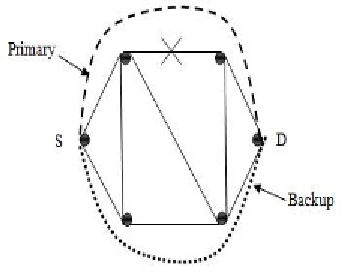
2.2. Path-Protection
In path-protection, network resources (such as bandwidth, buffer, and process capacity)
are saved for a unique path protection for the primary working path. Thereat, there is no
anticipation which link along the primary working path will fail; the system allocates a
protection path, which is link-disjoint from the primary path (Figure4). Therefore, the primary
path does not have any subscriber link with its relevant path protection [11].
Figure 4. Path protection scheme.
When a link fails, the source and destination nodes on the failed link are informed, and
then the source node can redirect the failed traffic on the protection path (i.e., the
communication is switched to the protection path) [11]. As soon as a failure takes place, an
error warning is sent to the source and destination of each affected connection. Each pair of
the source and destination nodes acts for communication switching from the main path to the
backup path [13].