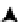Database Reference
In-Depth Information
Figure
10-2
represents the resource and locks discussed in this section. The resource master instance has a BL
resource allocated to protect the block in discussion. Two GCS (Global Cache Services) locks also have been acquired.
However, there is a minor distinction to be made between these two GCS locks, namely, GCS client and GCS shadow:
if the buffer represented by the resource is resident in the local buffer cache, then the corresponding GCS lock structure
is known as the GCS client; if the buffer is resident in the remote buffer cache, then the lock structure is known as
GCS shadow. A GCS client points to lock element, which in turn points to a buffer header structure. The buffer header
structure holds a pointer to the buffer in the buffer cache.
x$BH
Buffer
BH
Buffer
BH
LE
LE
x$LE
GCS
Client
GCS
Shadow
GCS
Shadow
x$KJBL
Resource
[0xb4][0x4],BL
x$KJBR
Resource Master instance
Owning instance
Figure 10-2.
Resources and locks
Fixed table x$kjbr externalizes resource structures, x$kjbl externalizes BL locking structures, x$le externalizes the
lock elements, and x$bh externalizes the buffer header structures.
The query in Listing 10-2 can be used to probe the internal structures further. (I should point out that this SQL
statement has no practical value, it is provided purely to help you understand the internal structures.) In 12c, this
statement must be executed in a container database (CDB) if the database is a CDB. You may be able to research the
internal structures further using the script in Listing 10-2.
Listing 10-2.
Lock_to_buffer
set lines 120
col kjblname format a30
col kjblname2 format a20
col kjblgrant format a10
col kjblrole format 9999
col kjblrequest format A10
set verify off
select /*+ leading (c a b ) */ b.kjblname, b.kjblname2 ,
b.kjblgrant, b.kjblrole, b.kjblrequest , b.kjblmaster, b.kjblowner
from x$le a , x$kjbl b, x$bh c