Hardware Reference
In-Depth Information
•
Point-to-point
—Bluetooth products (as well as Wi-Fi products in the ad hoc mode) use the
point-to-point topology. These devices connect directly with each other and require no access
point or other hub-like device to communicate with each other, although shared Internet access
does require that all computers connect to a common wireless gateway. The point-to-point
topology is much less expensive per unit than a star topology. It is, however, best suited for
temporary data sharing with another device (Bluetooth) and is currently much slower than
100BASE-TX networks.
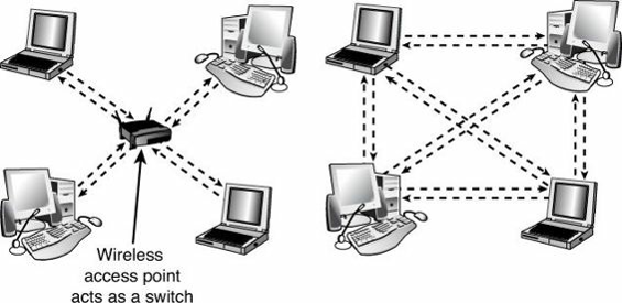
Figure 17.18
shows a comparison of wireless networks using these two topologies.
Figure 17.18. A logical star topology (left) as used by IEEE 802.11-based wireless Ethernet in
infrastructure mode compared to a point-to-point topology as used by Bluetooth and 802.11 in
ad hoc mode (right).
Wireless Network Security
When I was writing the original edition of
Upgrading and Repairing PCs
back in the 1980s, the
hackers' favorite way of trying to get into a network without authorization was discovering the
telephone number of a modem on the network, dialing in with a computer, and guessing the password,
as in the movie
War Games
. Today, war driving has largely replaced this pastime as a popular
hacker sport. War driving is the popular name for driving around neighborhoods with a laptop
computer equipped with a wireless network card on the lookout for unsecured networks. They're all
too easy to find, and after someone gets onto your network, all the secrets in your computer can be
theirs for the taking.
Because wireless networks can be accessed by anyone within signal range who has a NIC matching
the same IEEE standard of that wireless network, wireless NICs and access points provide for
encryption options. Most access points (even cheaper SOHO models) also provide the capability to
limit connections to the access point by using a list of authorized MAC numbers (each NIC has a
unique MAC). MAC address filtering designed to limit access to authorized devices only.
Although MAC address filtering can be helpful in stopping bandwidth borrowing by your neighbors,
it cannot stop attacks because the MAC address can easily be “spoofed” or faked. Consequently, you
need to look at other security features included in wireless networks, such as encryption.
Caution