Information Technology Reference
In-Depth Information
parameters. Firstly
A
selects a random value
R
and maps its plaintext message to a point
P(a
3
, b
3
)
on the elliptic curve structure. Then
A
constructs
the ciphertext message
C
which is represented by
two points
C
1
and
C
2
on the elliptic curve. The
ciphertext is produced based on the following
equations:
the need for an end-to-end round trip to a lookup
repository to obtain a public key certificate. To
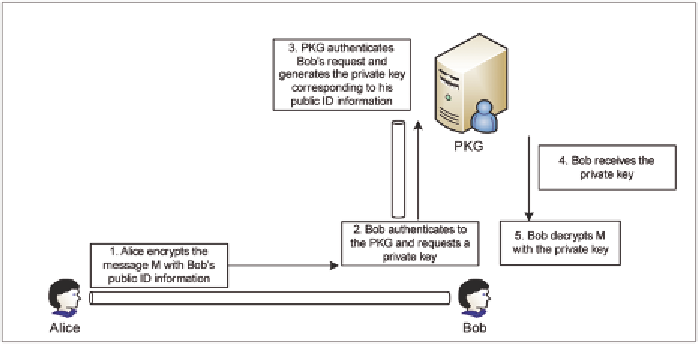
decrypt a message, the receiver authenticates to
a trusted Private Key Generator (PKG) which
generates the respective private key correspond-
ing to the public identifier and securely deliver
it to the requestor to be used in the decryption
process. In IBE, the principal's private keys are
refreshed periodically thus eliminating the need for
certificate revocation mechanisms and updates as
is the case in traditional public key infrastructures
(PKIs). This is illustrated in Figure 2.
Note that the public identifier can include
timing and access control information that aids
in 1) controlled management of the validity of
private keys, 2) securing the privacy of data on
non-trusted central storage, 3) protecting data
even in the cases of compromised communicating
entities, and 4) providing flexible access control
and authorization mechanisms to network and
storage data.
These features make IBE schemes very attrac-
tive for operation in BSN environments. More on
this will be presented when discussing the BSN
privacy protocols in the sixth section.
C
1
= R ×X(a
1
, b
1
) C
2
= P(a
3
, b
3
) + R × Y(a
2
, b
2
)
The Decryption Phase: in this phase an entity
B
receiving the ciphertext message
C
encrypted
with its public key uses its private key
K
to decrypt
the message and obtain the plaintext
P
.
B
retrieves
the plaintext
P
based on the following equation:
P(a
3
, b
3
) = C
2
- (K× C
1
)
. The keen reader may
replace
C
1
and
C
2
with their values calculated
in the encryption phase to prove that
C
2
- (K ×
C
1
)
is indeed the plaintext
P
determined by the
encrypting entity
A
.
IBE is a public-key cryptosystem whose public
key can be any arbitrary string. It was proposed by
Shamir in the mid 1980's to simplify certificate
management in email systems. The first practical
IBE was presented by Boneh and Franklin (2001).
With IBE schemes, the encrypting principal can
directly encrypt the message with the known
public identifier of the recipient thus avoiding
Figure 2. IBE high-level operation
Search WWH ::

Custom Search