Database Reference
In-Depth Information
Oracle Enterprise (API) Gateway
From the diagram in the
Risk mitigation design rules
section, you can see that OEG is the
product with highest concentration of core SOA security patterns. What are the common
requirements for such a tool to be trusted?
Vendor-neutral (generic) requirements
Some information about the requirements can be found on OWASP (search for
OWASP
XML Security Gateway Evaluation Criteria Project
), but a list of
twenty or forty criteria is too small. Our actual list has almost 200 positions and comprises
technical requirements of three different commercial SGs. Oracle is one of them. We en-
courage you to read some technical whitepapers about its capabilities as it is beyond the
scope of this topic.
Pass-through proxy with HTTP header verification
Number 5 in the OWASP top 10 is directly related to the complexity of security tools and
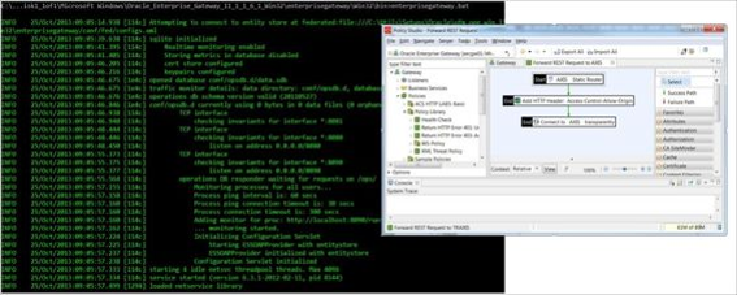
mechanisms. In our experience, OEG proved to be amazingly simple in installation, main-
tenance, and development (see the previous screenshot). Right after unpacking, you will
get a resilient and simple environment and an easy to start/stop and monitor. Policy Studio
(main development tool) is not exactly Eclipse-style, so it will take time some time to adapt
after OSB with its traditional request-response pipelines; however, in an hour, you will be
Search WWH ::

Custom Search