Database Reference
In-Depth Information
such as
DeMilitarized Zone
(
DMZ
). The application is well-layered and runs as a man-
aged code on JVM, but no WLS or OSB is required. So it's very lightweight on one hand
and reasonably protected from buffer stack overflow attacks by JVM features on the other.
Surely, the latest Java security updates must be applied promptly as certain risks related to
JVMs' security holes will exist, but this calculated risk is justified by the possibility to run
on the newest versions of OS and JDK as unmanaged gateways, because versions some-
times lag behind due to longer implementation time. Obviously, older OS releases are ex-
posed longer to the evaluation of vulnerabilities, giving more opportunities to hackers. Al-
though we do not really want to participate in the managed versus unmanaged code
clashes, the unmanaged Intel Expressway Service Gateway in our tests produced a stun-
ning 10 K tps 3 K SOAP message on two really modest dual core CPU servers.
At the same time, Oracle Gateway was almost as good, showing pretty similar figures.
Thus, the choice is yours.
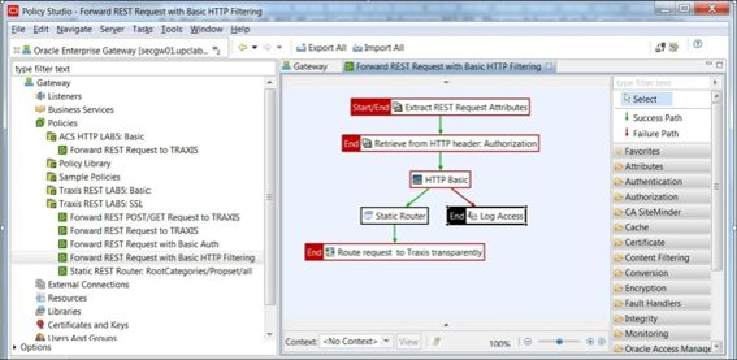
Oracle API Gateway Policy Studio
The option to choose the physical realization of this technical layer again comes from the
following principles, opening the door for vendor-neutral security implementation. What
must be strictly observed though is the compliance with common security standards:
Search WWH ::

Custom Search