Information Technology Reference
In-Depth Information
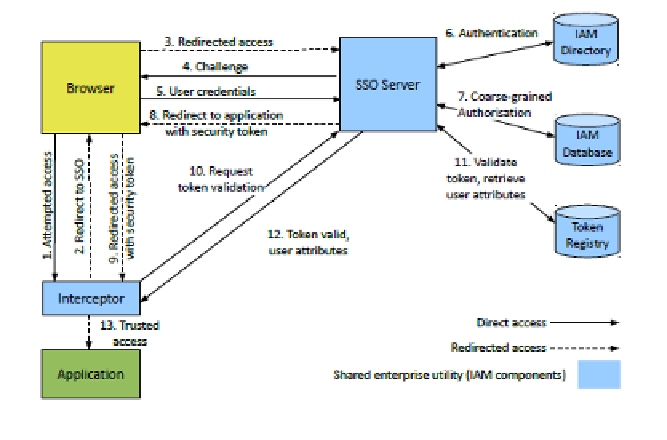
Using CAS to Centralise Enforcement of Authorisation Rules
One idea that occurred to us was to ask why CAS could not perform a
coarse-grained authorisation check against the IAM database right after the
authentication check against the IAM directory. Wouldn't that be more
guaranteeably secure from an auditor's perspective than just passing back
user attributes and leaving enforcement to each application's interceptor?
In other words, how about a process as shown below, where CAS actively
blocks
access if step 7 fails?
Fig 33: Centralised enforcement
Well, even though CAS has historically been an authentication mechanism
for distributed systems and not really an authorisation system, it is after all
an Open Source product, so it can be modified to perform this function with
very little effort.
When we explored this design option however, we encountered some
usability concerns that neutralised its minor edge in auditability. These
issues could be fairly universal, so you should think about them too.
What should CAS do if a user is correctly authenticated but doesn't have
access rights to the application they are trying to access? Should it just
display an error page?