Information Technology Reference
In-Depth Information
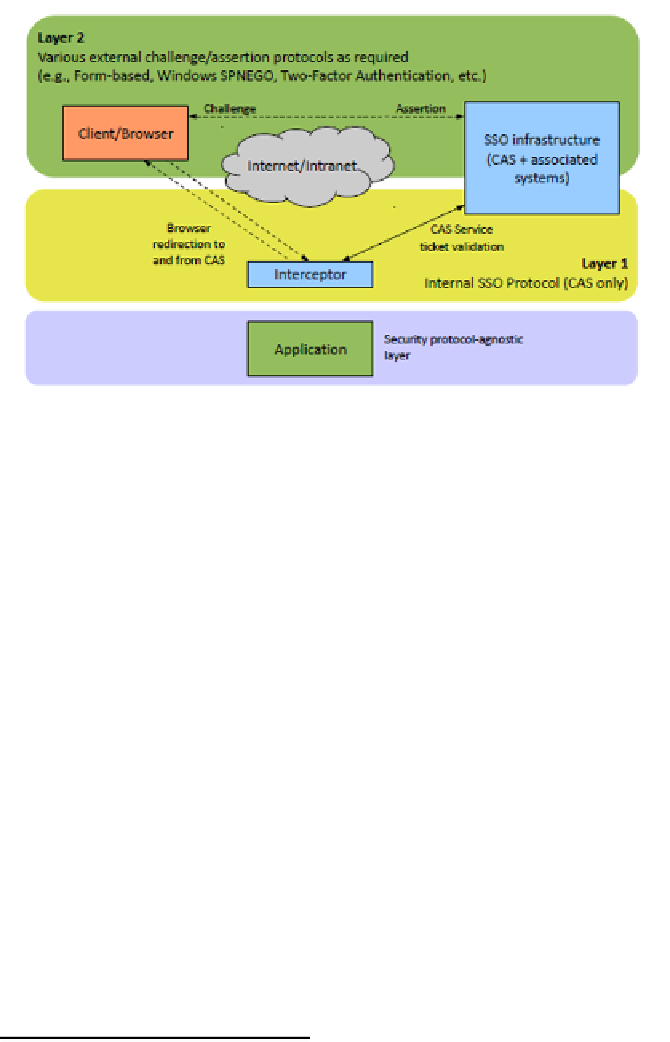
The Two-Layer Protocol Architecture is illustrated below:
Fig 19: Two-Layer Protocol Architecture
The next three sections will illustrate the utility of the Two-Layer Protocol
Architecture when we extend our Access Management infrastructure to
cover three different situations:
1.
LAN-based Single Sign-On using SPNEGO
2.
Two-Factor Authentication using SMS One-Time Tokens
Federated Identity using SAML2
24
3.
24
There is a potential problem with using the Two-Layer Protocol Architecture for
federated identity situations, which we will cover when we get to that discussion.