Information Technology Reference
In-Depth Information
Central Authentication Service and the CAS Protocol
In the 1980s, MIT developed an authentication system for distributed
applications that would work even over an untrusted network. The protocol
was called Kerberos, and it has since become the most successful Single
Sign-On mechanism used in the industry.
Yale University then took the Kerberos idea and implemented a version
called CAS, tailored to web applications. While the tokens used in CAS are
not
kerberized
tickets (i.e., they don't use the same formats that Kerberos
does), the types of components and the sequence of interactions between
them is an exact analogue of Kerberos.
CAS is a product that is extremely popular in academia, with most major
universities using it to secure their websites and web applications and
provide Single Sign-On to them. However, it has not been as popular in
corporate circles, and the reason for that is probably just corporate
snobbery with regard to academia! There is certainly nothing deficient in the
product that either we or our auditors could find. We believe you will find
CAS to be an extremely efficient, secure and maintainable piece of software.
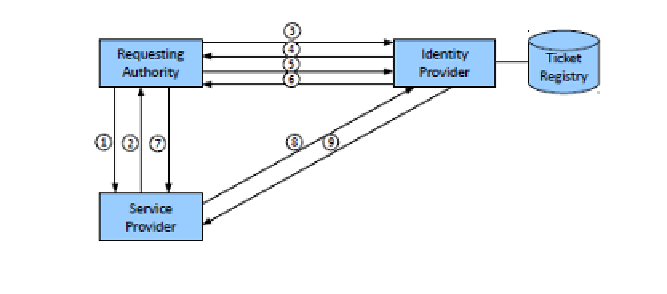
Here is the Kerberos/CAS authentication model at a glance, using the
appropriate terminology:
Fig 16: Kerberos/CAS model
1.
The Requesting Authority (RA), which could be any application but
specifically a browser in the CAS implementation, tries to access an
application (the Service Provider or SP). The SP is nothing but a web
application in the CAS model.