Information Technology Reference
In-Depth Information
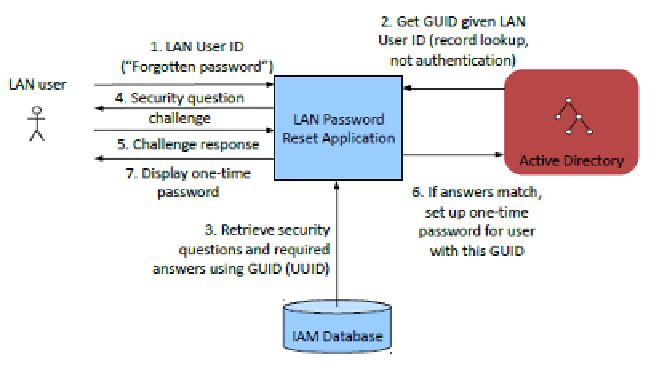
Fig 60: Resetting LAN passwords
Of course, all password reset requests are sensitive from an audit/security
perspective, so they should be logged and monitored.
This is another example of how decoupling user identity with a UUID/GUID
makes it really simple to integrate components and develop inexpensive
solutions to potentially tricky problems. Commercial off-the-shelf solutions
tend to be more expensive and yet have limitations that a bespoke solution
based on a loosely-coupled architecture does not suffer from.