Information Technology Reference
In-Depth Information
Appendix A - Typical Security Requirements from an IAM
System
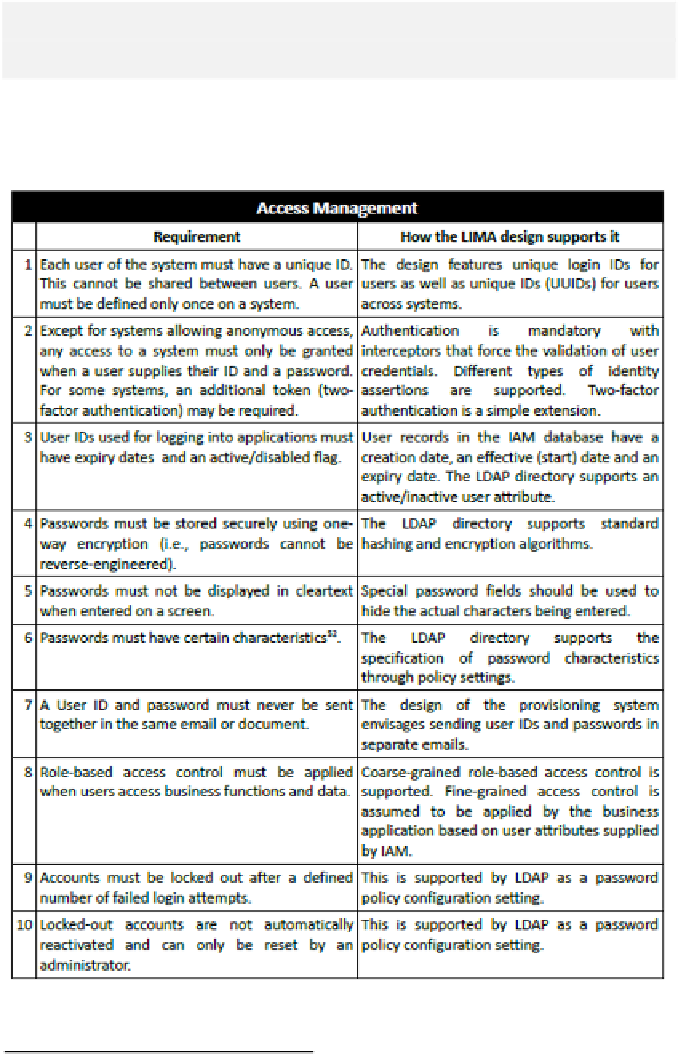
Security/audit staff tend to expect certain core features in an IAM system, as
listed below. While the LIMA approach supports them, you must ensure that
your design actually meets them.
52
Table 3: Access Management Requirements
52
Examples of password characteristics are minimum length, combinations of
alphanumeric, numeric and special characters, expiry period, uniqueness history,
change on first login or reset, etc.