Database Reference
In-Depth Information
C
i
= L(user)
K = K
Ci
Set i = 1
t
i
= D (K, E (K, t
i
))
t
i
[TC] ≤ L(user)
No
Ye s
i = i + 1
Set j = 1
t
i
[A
j
] ∈ [A
i
]*
j = j + 1
Ye s
No
t[A
j
] = E (K, t
i
[A
j
])
t[A
j
] = null
t[PK] = t´[PK] and
t[TC] = t´[TC]
Ye s
No
Tuple t´ will be
replaced by t
Tuple t will be
inserted
End
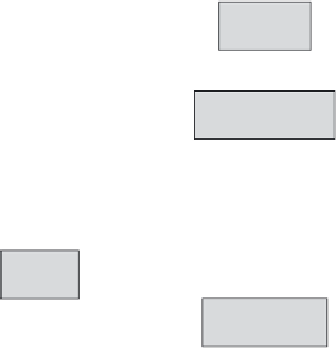
Figure 5.5
Flow chart for the uplevel operation in the encryption-based multilevel database
model. (R. Haraty and N. Bekaii. 2006.
Journal of Computer Science
2 (1): 19-28.)






























Search WWH ::

Custom Search