Database Reference
In-Depth Information
C
i
= L(user)
K = K
Ci
Set i = 1
Ye s
t
i
[TC] = L(user)
No
i = i + 1
t
i
= D (K, E (K, t
i
))
t
i
[TC]
≻
L(user)
Ye s
No
t
i
satisfy P
Ye s
Mark to be deleted
by high user
Detele ti
i
No
End
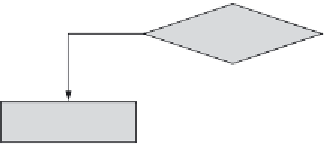
Figure 5.2
Flow chart for the delete operation in the encryption-based multilevel database
model. (Y. Elovici et al. 2004.
Proceedings of International Conference SDM,
28-40.)
where R is the relation name;
[A
1
,A
2
,...,A
n
]
are the attribute names;
and P is a predicate expression that may include conditions involving
the security classification attributes. Only those tuples
t
∈
r
that have
t
[
TC
] ≤
L
will be decrypted by key according to the classification level
of the subject that executes the SELECT statement and will be taken
into the calculation of P.
For those tuples
t
∈
r
that satisfy the P predicate expression:
• If a decrypted tuple satisfies the predicate expression, this
tuple will be included in the result of the SELECT statement.
Figure 5.3 illustrates the flow chart for the select operation in the
encryption-based multilevel database model.





















Search WWH ::

Custom Search