Information Technology Reference
In-Depth Information
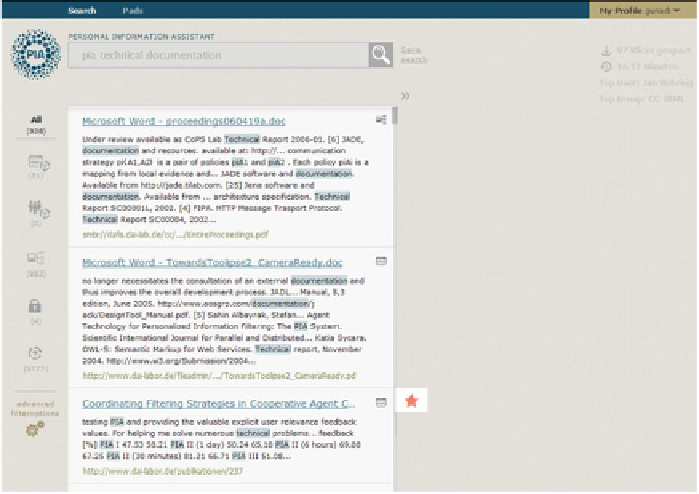
Fig. 4.8
Our web-client showing search results from the main department network, local desktop,
and department network
and forwards this information to the search agents. The search agents process in turn
the search query along with the user's credential in order to filter out the relevant
documents. This process allows the search system to return search results containing
only documents accessible to the user.
4.6 Conclusion and Outlook
In this chapter we discussed the application of secure distributed information retrieval
in enterprise environments. Focusing on the example of Suzanne and her workplace
environment, we illustrated the challenges employees face in an enterprise envi-
ronment. Data repositories like email accounts, file server, or web pages provide
the employees with important information needed to complete their daily tasks. An
employee should decide which repositories are important and must search these
repositories to find the relevant files for information gathering task.
Based on this example we first described the distinctive characteristics of enter-
prise environments. These characteristics, such as the heterogeneity of the available
data, security policy, and the distributed nature of the available data repositories,
should be addressed to create an enterprise search system. Enterprise search sys-
tem can be implemented in two forms: (1) by relying on a single centralized index
Search WWH ::

Custom Search